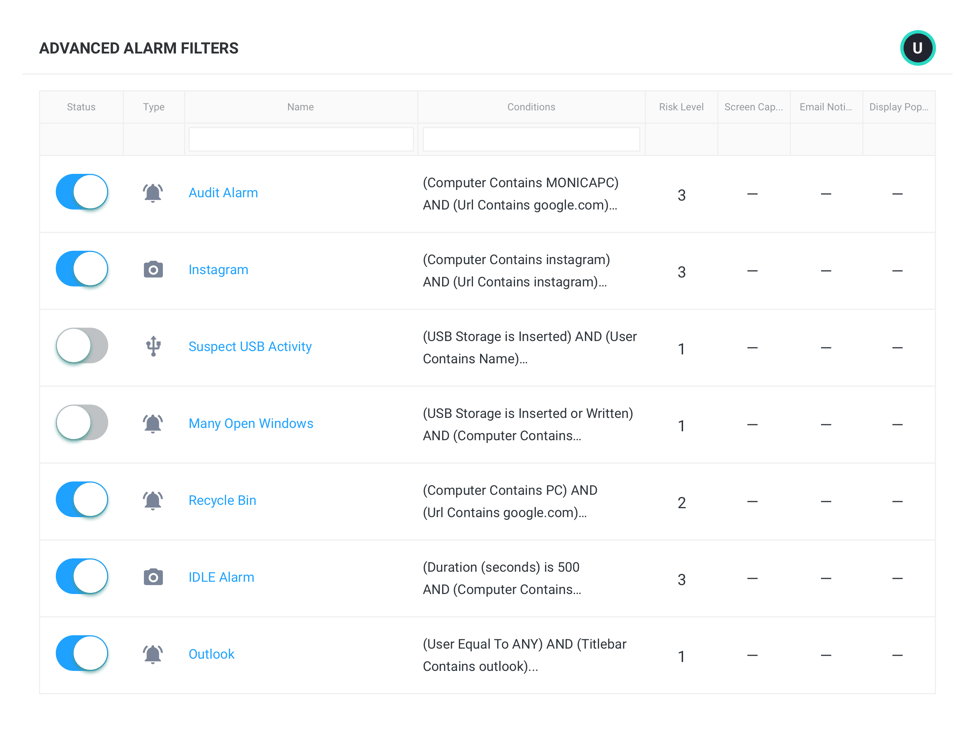
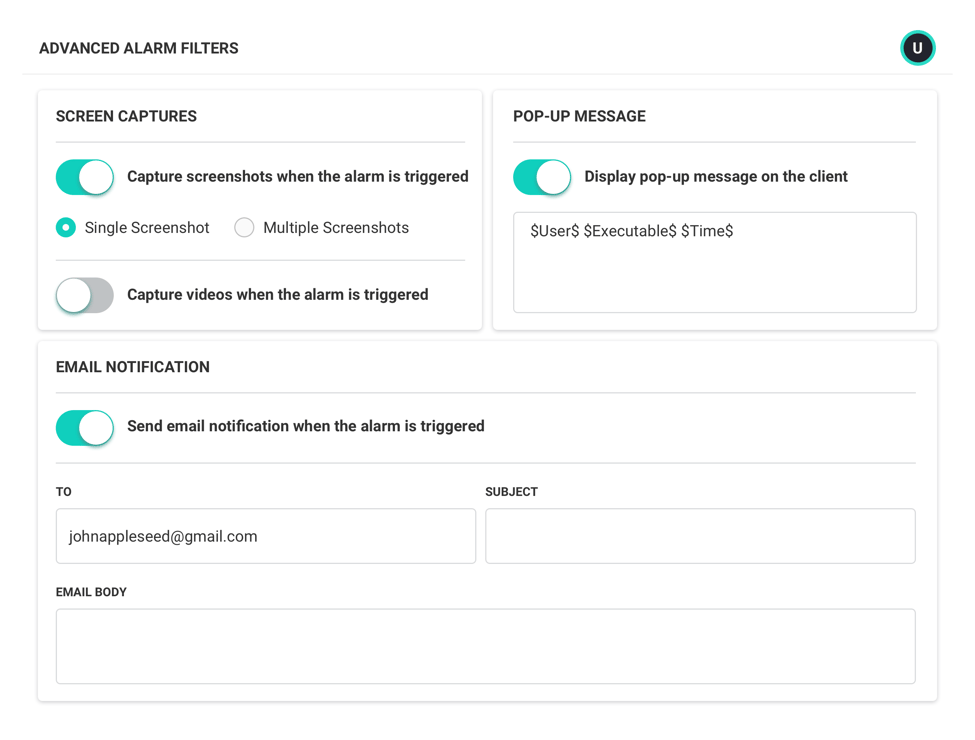
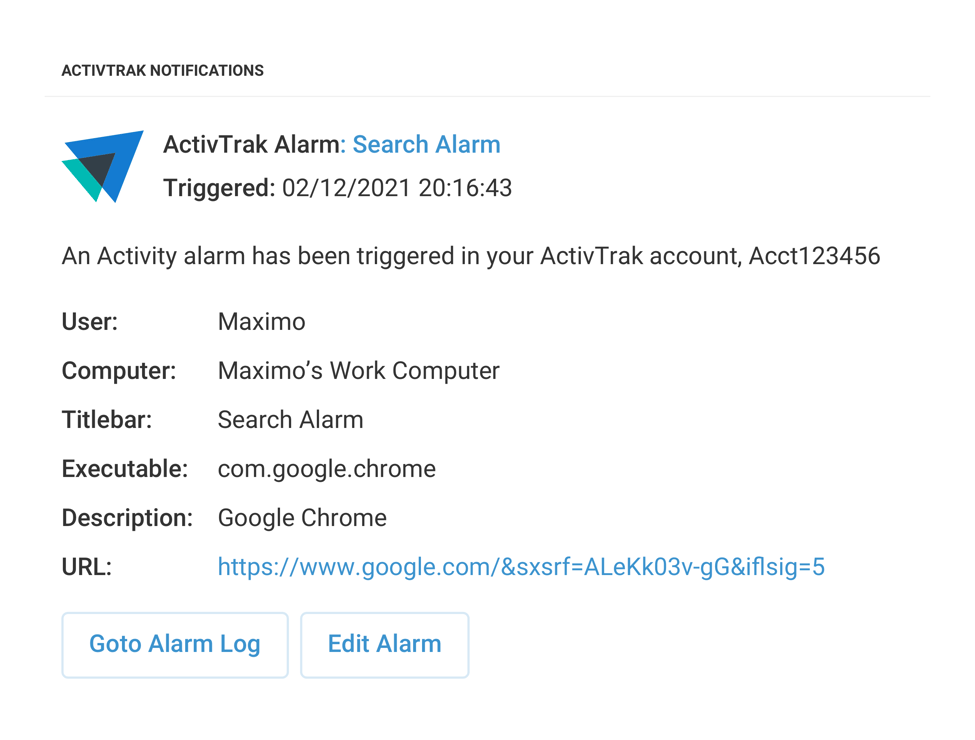
Pre-Built Alarms
Leverage pre-configured alarms out-of-the-box to help you track and get alerted to activities of interest.
- View user activities to see patterns of behavior, how time is spent and workflow bottlenecks.
- Identify USB device activity or unauthorized file sharing to control usage and protection of sensitive data.
- Get alerted on attempts to access blocked domains.
- Track activities such as deletion of users or removal of agents from computers.