The Challenge:
How to Ensure Data Privacy and Compliance
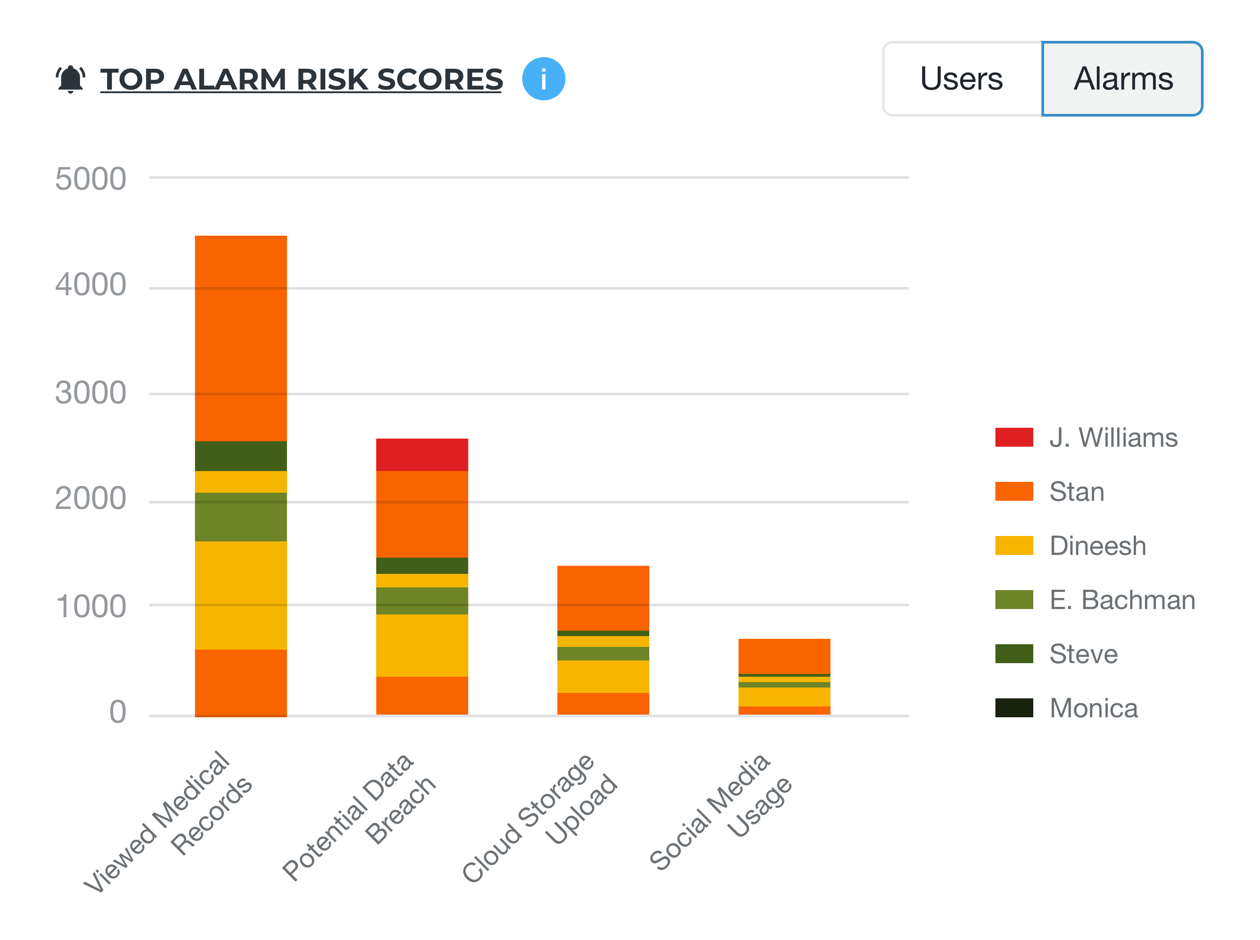
Organizations collect more data than ever before which comes with the necessary responsibility of how this information is stored, shared, protected and used. Data privacy and compliance reporting to adhere to regulations has become a critical part of managing a business. There are a number of challenges to balancing data privacy and compliance reporting without sacrificing employee productivity including:
- Managing legal issues and differing regulations across geographies.
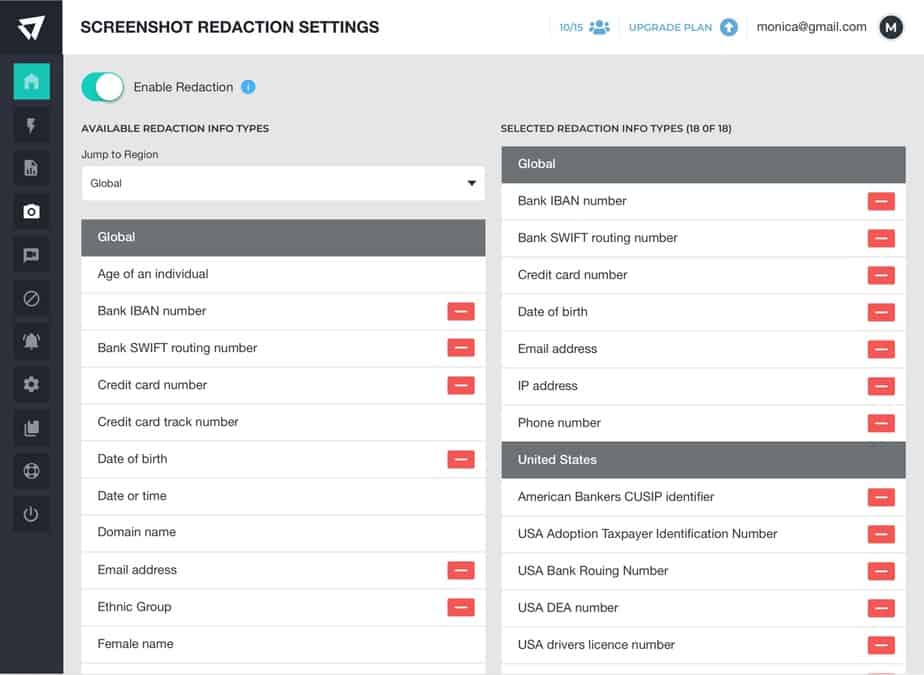
- Ensuring data collected adheres to security and compliance policies.
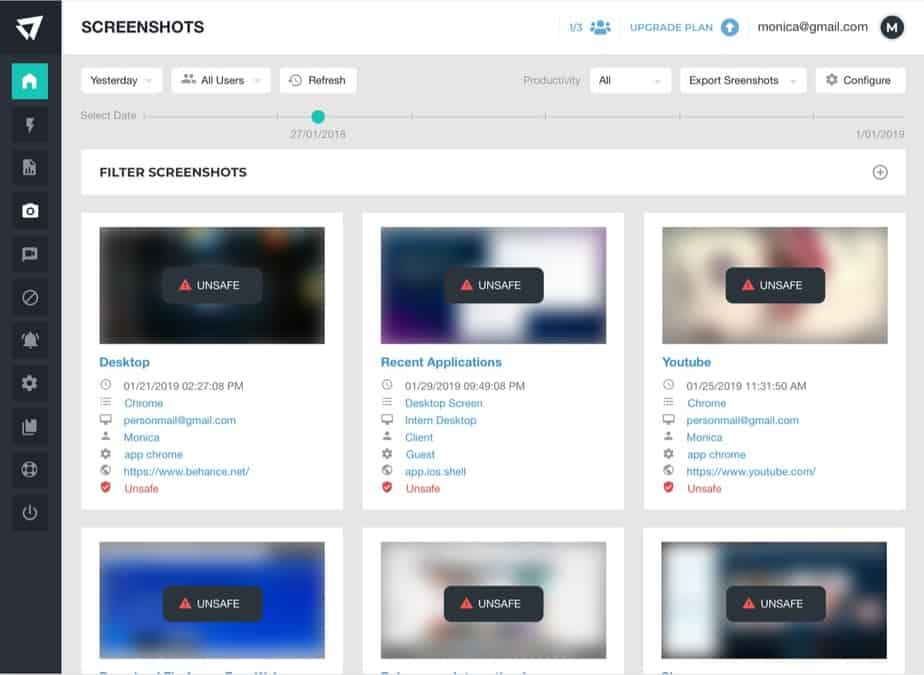
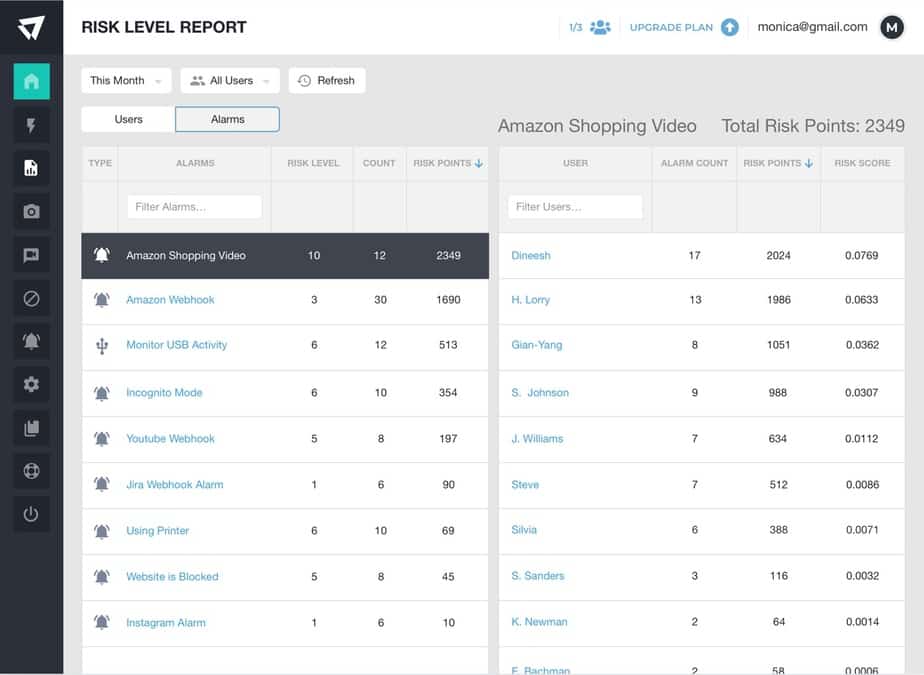
- Identifying employee improper handling and safeguarding of data.
- Protecting employee data privacy to ensure it is not violated.
- Mitigating breach potential from outsourced &/or remote employees.
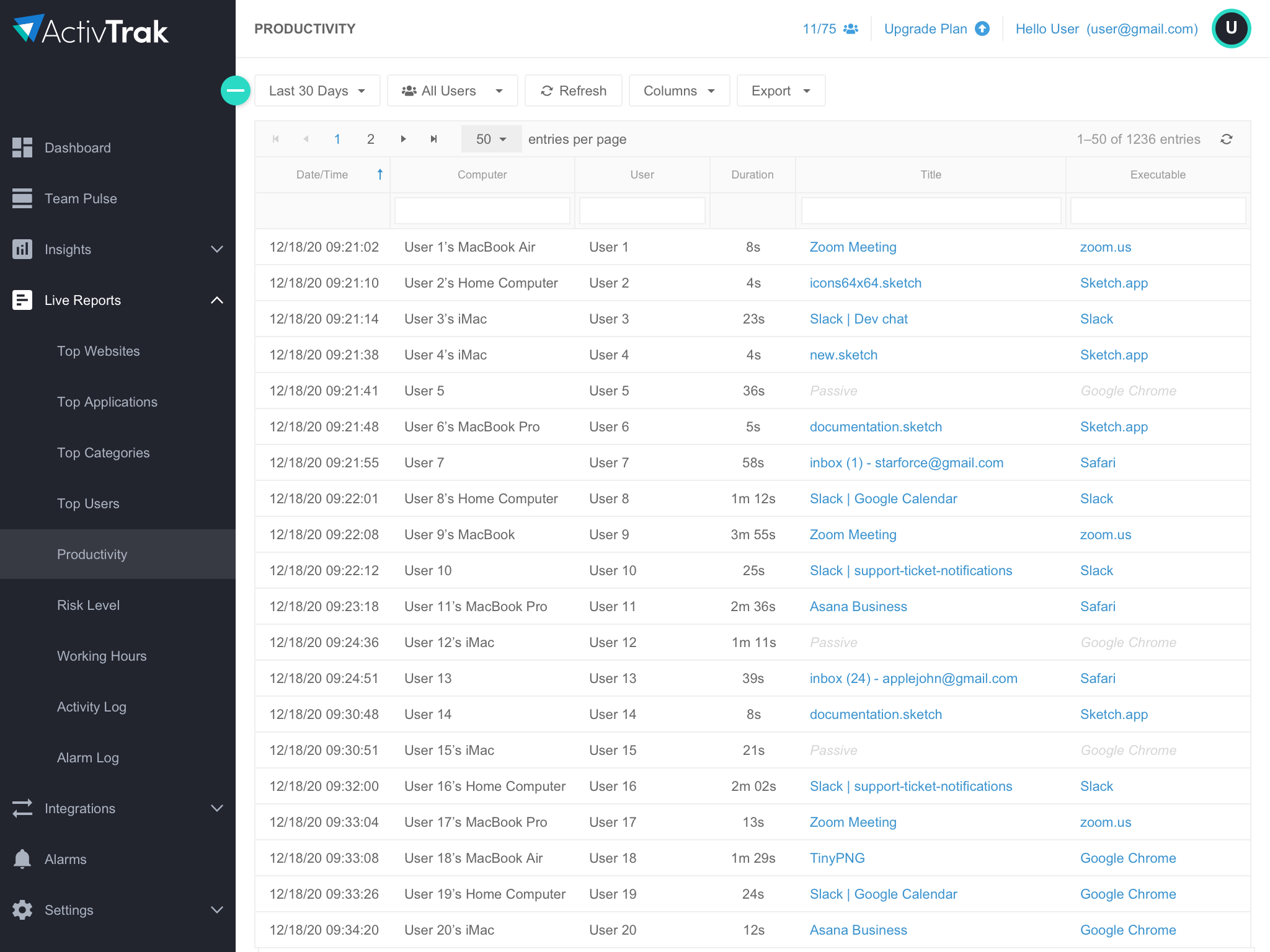
Tools to automate workflows and manage and monitor data flow through a user activity log all have key roles to play in managing data privacy, compliance reporting and risk.